Data handling and security
This section includes information about Foglight access control, data protection, and secure network communication. It also describes how Foglight security features meet the National Institute of Standards and Technology (NIST) recommended federal information security standards as detailed in the Federal Information Security Management Act (FISMA).This section covers the following key areas:
What data are we uploading?
The Foglight Agent Manager (FglAM) collects system configuration and performance metrics from monitored connections in your Foglight environment and then periodically uploads that data to Foglight Cloud. From the uploaded data and subsequent analysis, Foglight Cloud is able to generate a picture of your system’s health and performance. Executed SQL and the query plans used to execute the SQL may contain fragments of data by way of string literals. At request, string and numeric literals are replaced to prevent any accidental/unexpected upload of sensitive data.
How is customer data transferred from the Foglight Agent Manager to the cloud?
All communication from the Foglight agent managers to Foglight Cloud is done via HTTPS on port 443.
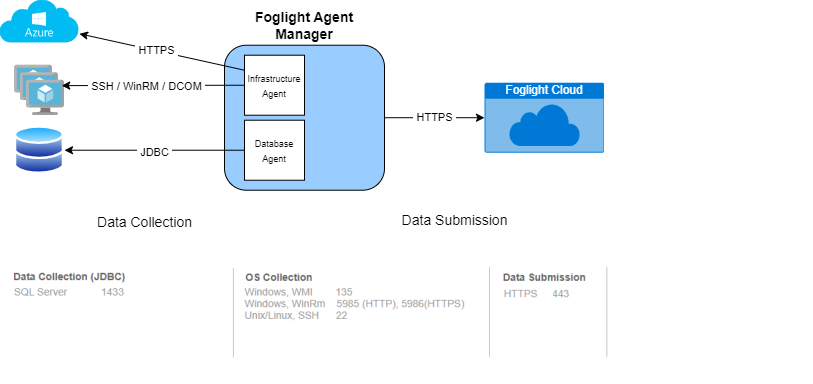
In the customer environment the communication between the agent manager and the monitored target is done using listed protocols in regular open ports. For example, to monitor default instance of SQL Server, port 1433 should be opened.
Where is customer data stored?
Foglight® agents collect data and store it in the repository database, which is secured using user access controls and encrypted at rest. All data is uploaded to Azure data centers in the USA or Germany, based on the customer’s preference.
How long is customer data kept?
The duration of time data uploaded to Foglight Cloud is kept, varies depending on the type of data. Usually, it is kept for no more than a year at different granulation levels.
How Foglight protect credentials?
When installing Foglight agents it is typically necessary to enter credentials for the user accounts that are on the monitored resources, including the host and database. These credentials are entered through the Foglight user interface and give an agent access to applications or operating systems on the monitored hosts.
Foglight platform includes a central credential service that manages agent credentials. A lockbox contains a set of credentials and keys for their encryption and decryption. Releasing a lockbox to a credential client enables the client to release the credentials to the agent instances managed by that client, thereby granting the agent instances access to the monitored system.
Protection of Data Collection Infrastructure
There are many types of Foglight® agents; most communicate with the Foglight Server through a provided client component— the Foglight Agent Manager (FglAM).
The Agent Manager can be installed without administrator access, but such access is required to enable startup scripts or Windows® services to allow automatic launching of the Agent Manager upon machine reboot. The Agent Manager can be initially installed on a monitored host through an installer GUI, a text-based console installer, or a command-line silent mode (suitable for mass deployment using customer-provided tools).
Once installed, the Agent Manager component manages the life cycle of a number of hosted agents and provides a central communications link between those agents and the Management Server. Hosted agents and the Agent Manager can be upgraded from the Management Server using this central communications link.
Agents requiring privilege escalation
Some data collection agents hosted by the Agent Manager require administrator privileges to perform their assigned tasks. In order to avoid running the entire client host with the required privileges, Foglight® uses a privilege escalation mechanism to create the required access for the agents that need it.
The Agent Manager, by default, uses the well known sudo facility (a very fine-grained configurable system) to implement privilege escalation. Sudo can be configured to allow only specific applications to be launched with escalated privileges, and the privileges provided to each launched application can be independently controlled. In addition, sudo allows the administrator to limit the parameters passed to each application; this facility is central to configuring a secure system with the Agent Manager.
The Agent Manager also provides an alternative setuid root-based launcher. This launcher is only intended for use in demonstration installations with minimal security needs, where the burden of properly configuring sudo for fine-grained access control would hinder a timely demonstration. Quest does not recommend that this setuid root-based launcher be configured as part of Foglight’s standard installation instructions.
How is the Data Protected
Foglight use the JavaTM Cryptographic Extension library for cryptographic operations.
| Data | Encryption in normal mode | Remark |
|---|---|---|
| Agent Credentials | RSA 2048-bit | Using automatically generated RSA key as encryption key, the key is protected by lockbox password |
| Lockbox Credentials | AES 256-bit | Using default Foglight encryption key |
| Sensitive data in ASP | AES 256-bit | Using default Foglight encryption key |
Foglight Agent Manager uses the Java Cryptographic Extension library for cryptographic operations.
| Data | Encryption in normal mode | Remark |
|---|---|---|
| Keystore password | AES 256-bit | Using default Agent Manager encryption key for encrypting keystore passwords. |
| Agent Credential | RSA 2048-bit | Using the lockbox key for decrypting the agent credentials retrieved from Foglight Management Server. |
| DH Key Exchange | DH 2048-bit | Using 2048-bit modulus to exchange DH session key between Foglight Management Server and Agent Manager. |
| Lockbox key | AES 256-bit | Using the DH session key for encrypting or decrypting the lockbox key. |
| Agent Properties Cache | AES 256-bit | Encrypting or decrypting the cached agent properties data. |
SSH Communication between Agents and monitored resources
The following encryption algorithms are supported by the Foglight Agent Manager for SSH connections to monitored resources.
Key Exchange Algorithms
- curve25519-sha256
- curve25519-sha256@libssh.org
- curve448-sha512
- ecdh-sha2-nistp521
- ecdh-sha2-nistp384
- ecdh-sha2-nistp256
- diffie-hellman-group-exchange-sha256
- diffie-hellman-group18-sha512
- diffie-hellman-group17-sha512
- diffie-hellman-group16-sha512
- diffie-hellman-group15-sha512
- diffie-hellman-group14-sha256
- diffie-hellman-group14-sha1
- diffie-hellman-group-exchange-sha1
- diffie-hellman-group1-sha1
Host Key Algorithms
- ecdsa-sha2-nistp256-cert-v01@openssh.com
- ecdsa-sha2-nistp384-cert-v01@openssh.com
- ecdsa-sha2-nistp521-cert-v01@openssh.com
- ssh-ed25519-cert-v01@openssh.com
- rsa-sha2-512-cert-v01@openssh.com
- rsa-sha2-256-cert-v01@openssh.com
- ecdsa-sha2-nistp256
- ecdsa-sha2-nistp384
- ecdsa-sha2-nistp521
- ssh-ed25519
- sk-ecdsa-sha2-nistp256@openssh.com
- sk-ssh-ed25519@openssh.com
- rsa-sha2-512
- rsa-sha2-256
- ssh-rsa
- ssh-dss
Ciphers
- chacha20-poly1305@openssh.com
- aes128-ctr
- aes192-ctr
- aes256-ctr
- aes128-gcm@openssh.com
- aes256-gcm@openssh.com
- aes128-cbc
- aes192-cbc
- aes256-cbc
MAC algorithms
- hmac-sha2-256-etm@openssh.com
- hmac-sha2-512-etm@openssh.com
- hmac-sha1-etm@openssh.com
- hmac-sha2-256
- hmac-sha2-512
- hmac-sha1
Quest protect Personally Identifiable Information (PII)?
String and numeric literals may contain sensitive or Personally Identifiable Information (PII). Before transferring data to the Foglight Cloud environment, Quest replaces all string and numeric literals in SQL statements and queries with placeholder data. The placeholder data has no reference to the original data, cannot be reversed into the original data and has no association with the original data.
For more information refer to Configure Foglight Cloud to replace literals.

